As technology advances, ensuring the security of computer systems, networks, and applications becomes increasingly critical. One of the ways in which security professionals can assess the security posture of an entire digital ecosystem is by carrying out penetration testing, or pen testing for short.
Penetration testing is the authorized simulation of a real-world cyber-attack. This allows organizations to evaluate how strong their security systems are and identify what weaknesses or vulnerabilities are present, if any.
According to research by SNS Insider, the penetration testing market is expected to reach $6.98 billion in value by 2032, largely due to the continued advancement of cybersecurity threats. As a fundamental practice for assessing an organization’s security posture, pentests involve both the expertise of experienced security professionals and the use of powerful penetration testing tools.
Given the proliferation of these tools, I have come up with a list of the top penetration testing tools available with their features, benefits, and drawbacks.
Penetration testing software comparison table
Here is a feature comparison of our shortlisted pen testing tools and how they stack up against each other.
| Compliance checks | Number of tests covered | Open-source / web-based | Reporting and documentation | Starting price | |
|---|---|---|---|---|---|
| Astra | Yes | 8,000+ | Web | Yes | $1,999 per year, one target |
| Acunetix | No | 7,000+ | Web | Yes | Contact for quote. |
| Intruder | Yes | Not specified | Web | Yes | $157 per month, one application |
| Metasploit | Yes | 1,500+ | Both | No | Contact for quote. |
| Core Impact | Yes | Not specified | Web | Yes | $9,450 per user, user per year. |
| Kali Linux | Yes | Not specified | Open-source | Yes | Completely free |
| Wire Shark | No | Not specified | Open-source | Yes | Completely free |
| SQL Map | No | Not specified | Open-source | Yes | Completely free |
Astra: Best for diverse infrastructure

Astra is a penetration testing tool solution with several automated testing features that combine manual with automated penetration testing features for applications, networks, API, and blockchain. With over 8,000 tests supported, this tool can help security professionals investigate vulnerabilities within a system. Astra covers different types of penetration testing, including web app pentest, cloud security pentest, and mobile app pentest.
As a comprehensive penetration testing solution, Astra covers many tests that can help organizations meet compliance standards. Some of the compliance standards that Astra can check include SOC2, GDPR, and ISO 27001. The Astra tool also integrates with GitLab, Jira, and Slack and infuses security into a continuous integration/continuous deployment (CI/CD) pipeline.
Why I picked Astra
I picked Astra for its Enterprise Web App subscription, which accommodates different infrastructures. In particular, it can be used on web, mobile, cloud, and network infrastructures, offering multiple targets across various asset types. This is on top of Astra’s 8,000+ available tests and its wide range of integrations with other popular software.
Pricing
Astra’s pricing is categorized into web app, mobile app, and AWS cloud security, each with different pricing.
- Web app: Scanner – $1,999/year, Pentest – $5,999/year, Enterprise – $9,999/year.
- Mobile: Pentest – $2,499/year and Enterprise – $3,999/year.
- AWS cloud security: Under this are the Basic and Elite plans, and both require users to speak to the sales team for a quote.
Features
- Covers 8,000+ tests scanning.
- Covers all tests required for ISO 27001, HIPAA, SOC2, and GDPR.
- Integration with GitLab, GitHub, Slack, and Jira.
- PWA/SPAs apps scanning support.
- Support through Slack and Microsoft Teams.
Integrations
- Slack workspaces.
- Jira.
- GitHub.
- GitLab.
- Azure.
- CircleCI.
Astra pros and cons
| Pros | Cons |
|---|---|
| Supports publicly verifiable pentest certificates, which can be shared with users. | What is supposed to be a free trial is charged at $1 per day. |
| Offers one of the widest testing coverages (over 8,000). | Support via Slack and MS Teams is only available on the Enterprise plan. |
| Tests are automated with AI/ML. | |
| Support via Slack or Microsoft Teams. |
Acunetix: Best for pentest automation

Acunetix by Invicti is a powerful pen-testing tool for web applications. The solution is packed with scanning utilities that can help penetration test teams quickly get an insight into over 7,000 web application vulnerabilities and provide a detailed report covering the scope of vulnerability.
Some of the notable vulnerabilities Acunetix can detect include XSS, SQL injections, exposed databases, out-of-band vulnerabilities, and misconfigurations.
Acunetix comes with a dashboard that can sort vulnerabilities into classes, such as critical, high, medium, and low. The tool is written in C++ and can run on Microsoft Windows, Linux, macOS, and the cloud.
Why I picked Acunetix
For businesses specifically looking for automated pentesting, I like Acunetix. It offers scheduled or recurring application scans, includes over 7,000 vulnerability tests, and generates useful insights before a scan is halfway through. I imagine it to be a great solution for organizations that want a no-nonsense pentest tool that saves them time without sacrificing overall security.
Pricing
Contact Acunetix for a quote.
Features
- Vulnerability categorization into an order of severity.
- Over 7,000 web app vulnerabilities are supported.
- Covers the OWASP Top 10 standard for developers and web application security.
- Scan scheduling functionality.
- Compatibility with issue-tracking tools like Jira and GitLab.
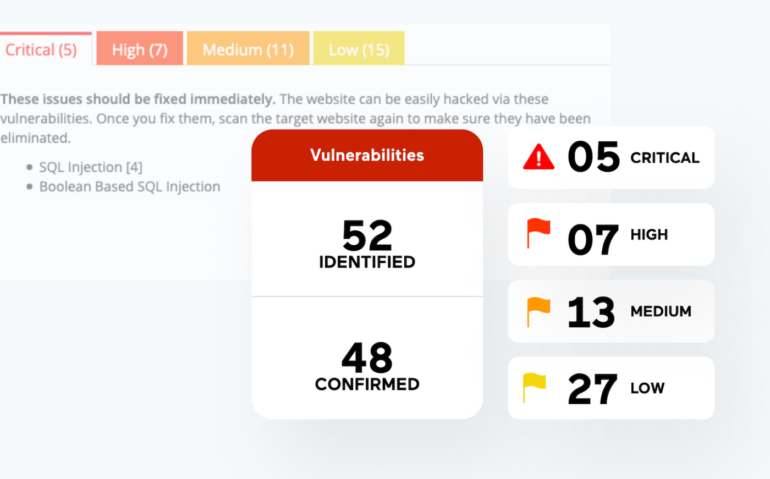
Integrations
- Jira.
- Azure DevOps.
- GitHub.
- GitLab.
- Bugzilla.
- Mantis.
Acunetix pros and cons
| Pros | Cons |
|---|---|
| Detected vulnerabilities are classified according to their severity level. | No pricing details for users. |
| Supports reporting and documentation. | Absence of a free trial. |
| Over 7,000 vulnerability tests are a broad coverage. | |
| Users can schedule one-time or recurring scans. | |
| Supports concurrent scanning of multiple environments. |
Features
- Cloud vulnerability scanning.
- Web vulnerability scanning.
- API vulnerability scanning.
- Compliance and reporting features.
- Internal and external vulnerability scanning.
Integrations
- Amazon Web Services (AWS).
- Drata.
- Jira.
- GitHub.
- GitLab.
- Google Cloud.
Intruder pros and cons
| Pros | Cons |
|---|---|
| Offers a 14-day free trial. | Does not specify the number of tests covered. |
| The availability of a demo makes it easier for first-time users to get started with the tool. | The 14-day free trial is only available under the Pro plan. |
| Auto-generates reports for compliance. |
Features
- Integrations via Remote API.
- Automated credentials brute forcing.
- Automated reporting capabilities.
- Task chains for automated custom workflows.
Integrations
- InsightVM.
- Python.
- Core Impact.
- Burp Suite.
- Project Sonar.
- Nexpose.
Metasploit pros and cons
| Pros | Cons |
|---|---|
| Offers a 30-day free trial. | The Framework version is limited in functionality. |
| Uses a simple web interface. | The Github download and setup method might be difficult for new users. |
| Has a free edition for developers and researchers. | |
| Available as open-source and commercial software. |
Core Impact: Best for collaboration

Core Impact, now a part of Fortra, ranks as one of the oldest penetration testing tools that have evolved alongside the current demands of a testing environment. The software can facilitate the process of attack replication across endpoints, network infrastructures, the web, and applications to reveal exploited vulnerabilities and provide suggestions for remediation.
Core Impact reduces the need for manual configuration during installation and testing. Users can easily define test scope and set testing parameters, and Core Impact does the rest. In addition, this tool can generate an attack map, giving users a real-time report of attack activities during testing.
Why I picked Core Impact
I selected Core Impact for its strong focus on team testing. It allows a number of security testers to interact with each in the same session. This allows testing teams to easily share findings and data, as well as smoother delegation of testing tasks. With Core Impact’s emphasis on shared workspaces, testing becomes more efficient and holistic as a result.
Pricing
Core Impact has three pricing plans:
- Basic: Starts at $9,450/user per year.
- Pro: Starts at $12,600/user per year.
- Enterprise: Request a quote.
Features
- Automated Rapid Penetration Tests (RPTs).
- Multi-vector testing capability that includes network, client and web.
- Vulnerability validation of third-party scanner results.
- Centralizes pen testing, from information gathering to reporting.
- Pen testing covers network security, web application, IoT security, and cloud security.
Integrations
- Metasploit.
- Cobalt Strike.
- PowerShell.
- Empire.
- PlexTrac.
Core Impact pros and cons
| Pros | Cons |
|---|---|
| Uses automation wizards to discover, test and report. | Pricing is very expensive. |
| Free trial available. | Free trial does not state how long the trial period lasts. |
| Offers broader cybersecurity services. | |
| New users can learn about the tool via a demo. |
Kali Linux: Best for technical users

Kali Linux is an open-source pen testing solution that runs on the Debian-based Linux distribution. The tool has advanced multi-platform features that can support mobile, desktop, Docker, subsystems, virtual machines, and bare metal testing.
As an open-source tool, professionals can easily customize it to match their testing situations. There is detailed documentation on using Kali’s meta packages to generate software versions for specific testing purposes. Kali also saves users the time to manually set up tools by adding an automated configuration system that optimizes the tool according to different use cases.
Why I picked Kali Linux
Kali Linux is my pick for technical and experienced pentesters looking for a powerful testing solution. It was designed with professional penetration testers in mind, offering a highly customizable architecture that lets pen testers build their own software version tailored to their needs.
I particularly appreciate how Kali Linux is upfront in saying that it’s made for veteran pentesters and experienced Linux users, not everyday consumers. This allows their tool to be as good as it can be for their chosen user-base instead of trying to accommodate all users, which may lessen overall quality.
Pricing
It is available completely free of charge.
Features
- Metapackages can be used for specific tasks.
- Offers Live USB Boot for easy booting from a USB device.
- Supports over 600 penetration testing utilities.
- Open-source development model can be accessed on GitHub.

Integrations
- AWS.
- Azure.
- Digital Ocean.
- Linode.
Kali Linux pros and cons
| Pros | Cons |
|---|---|
| Supports a wide array of versions. | Mostly ideal for advanced Linux users. |
| Available for free. | |
| Courses and documentation are available for new users. | |
| Multi-language support. |
Wireshark: Best for Unix OS

The Wireshark tool can analyze and test an organization’s network protocol for threats. The tool is a multi-platform penetration testing utility with useful features such as live capture, offline, and VoIP analysis.
As an open-source tool, Wireshark provides a lot of support for its users through documentation, webinars, and video tutorials. The tool also provides decryption features for arrays of protocols such as Kerberos, SSL/TLS, and WEP.
Why I picked Wireshark
I chose Wireshark for being a good pick for Unix OS users. As a completely free and open-source tool, Wireshark allows users to test network protocols and see what’s happening in both broad and fine detail. While it can be technically intimidating, I like the in-depth documentation it provides to users interested in using Wireshark for their specific testing needs.
Pricing
It is available for free.
Features
- Available for UNIX and Windows.
- Capture live packet data from a network interface.
- Display filters for sorting through and analyzing traffic streams.
- Supports offline and VoIP analysis.
Integrations
- AirPcap.
- YR20 network capture hardware.
- Inside Products.
- C5 SIGMA.
Wireshark pros and cons
| Pros | Cons |
|---|---|
| It is available for free and is open source. | Setup might be too technical for new users. |
| There is an export objects function for exporting test results. | Limited automated functionalities. |
| It can be used for decryption across a wide range of protocols. | |
| Quality documentation for new users. |
SQLMap: Best for detecting SQL injection attacks

For open-source lovers, SQLMap is an excellent penetration testing tool for detecting and exploiting SQL injections in applications. Penetration testers utilize the tool to hack databases and understand the depth of vulnerabilities.
In addition, SQLMap has a testing engine that can run several SQL injection attacks simultaneously, reducing the time spent running the test. Some notable servers supported on the platform are Microsoft Access, IBM DB2, SQLite, and MySQL.
It is also a cross-platform tool, supporting macOS, Linux, and Windows operating systems.
Why I picked SQLMap
For businesses looking to protect against SQL injection attacks, I strongly recommend having SQLMap on your list. It’s a high-quality pentest tool that’s designed to detect SQL injections automatically in all types of applications. It covers many injection attacks and techniques and has extensive support for numerous database management systems. SQLMap is free and has a good amount of documentation available online.
Pricing
Available for free.
Features
- Supports multiple SQL injection techniques.
- Automatic recognition of password hash formats.
- Support for cracking passwords using a dictionary-based attack.
- Can execute arbitrary commands and retrieve their standard output.
Integrations
- Burp Suite.
- Metasploit.
- Nmap.
SQLMap pros and cons
| Pros | Cons |
|---|---|
| Covers a broad range of SQL injection techniques. | Only suitable for command-line users. |
| Compatible with multiple database management systems like MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, and more. | |
| Available for free. | |
| Has good documentation. |
Key features to look for in penetration testing tools
Penetration testing solutions offer several features and use cases depending on the user’s objective. Below are the key features of penetration testing solutions.
Vulnerability scanning
Vulnerability scanning refers to the process of searching for weaknesses and loopholes in software applications, networks, and systems. A common technique used in pentesting, these scans can detect potential vulnerabilities, such as outdated software versions, misconfigurations, and known security flaws.
Network mapping and reconnaissance
Network mapping and reconnaissance refer to the process of gathering information and creating a visual representation of a network’s infrastructure and its connected devices. Before launching an attack, hackers typically gather information about their target.
Similarly, penetration testing tools assist with reconnaissance activities by mapping networks, identifying active hosts, and collecting information about the target infrastructure. This feature aids security professionals in understanding the organization’s digital footprint and potential entry points for attackers.
Traffic analysis and sniffing
Some penetration testing tools can analyze network traffic and capture packets. This capability allows security professionals to monitor and inspect network communication, identify potential vulnerabilities, and detect any suspicious or malicious activities. By analyzing network traffic, organizations can gain valuable insights into the security posture of their systems.
Reporting and documentation
Effective communication of vulnerabilities and recommended mitigation strategies is essential in the penetration testing process. Penetration testing tools offer reporting and documentation features to generate comprehensive reports detailing identified vulnerabilities, steps taken during testing, and recommendations for remediation. These reports aid in the prioritization and implementation of security measures and compliance verification processes.
Customization features
Different organizations have unique security requirements. These tools often offer customization options and extensibility features, allowing security professionals to tailor the testing process to their specific needs. Customization empowers organizations to focus on their most critical assets and assess vulnerabilities that are specific to their environment.
Frequently asked questions about penetration testing
What is the difference between vulnerability scanning and penetration testing?
Vulnerability scanning looks for weaknesses or holes in your organization’s computer network and reports it to the organization. Penetration testing, on the other hand, identifies system vulnerabilities and tries to exploit them. This evaluates how an organization’s security measures react during an attack.
Conducted by ethical hackers and DevOps engineers, pen tests simulate a real cyber attack against your organization’s security posture. Meanwhile, IT departments typically conduct vulnerability scanning to identify security gaps and provide actionable insights afterward.
As the two concepts overlap and diverge in various areas, other aspects like scope, goal, and cost must be considered. However, the description above is a quick overview of the two cybersecurity strategies side-by-side.
If you’re interested in a more in-depth comparison, you can check out our Vulnerability Scanning vs Penetration Testing feature.
How can penetration testing tools be used to assess network security?
Ethical hackers can do a “network pen test,” a type of penetration testing specifically targeting your organization’s network infrastructure. With the use of pen test tools, organizations can get a first-hand glimpse of how their network security systems either successfully or unsuccessfully defend against malicious actors trying to launch an attack.
Pen test tools can also highlight gaps or vulnerabilities within the network itself, which can involve firewall misconfigurations, outdated or buggy software, and unauthorized access, among others.
What are the limitations of penetration testing?
While pen tests can produce valuable insights regarding your organization’s security posture, they do have limitations. Here are a few:
- Results are restricted by the scope of the pen test, which can leave some areas excluded from the evaluation.
- Real attackers don’t have time constraints, while pen tests are time-bound.
- They can be costly and resource-intensive, which can be significant barriers to smaller organizations with limited resources.
- As humans, pen testers can make mistakes or miss vulnerabilities, leading to incomplete findings.
How do I choose the best penetration testing software for my business?
Given the avalanche of pen-testing tools available to security professionals, choosing the right software is often challenging. Here are key considerations to help you choose the best penetration testing software for your specific business needs.
Identify your pen testing goals
Before starting the selection process, clearly define your objectives for conducting penetration testing. Determine what you aim to achieve through the testing process, such as identifying vulnerabilities in your systems, assessing the effectiveness of your security controls, or meeting regulatory compliance requirements.
Understanding your goals will help you narrow down the software options that align with your specific requirements. Our comparison table shows that some of the tools are better than others for different scenarios.
Clearly define scope and budget for pen testing
Sometimes you think it’s ideal to test your entire system environment; however, defining the cost of testing your entire software ecosystem may convince you otherwise. Every organization has high and low vulnerability points. High-risk points are the areas that malicious actors can easily exploit. They can include application code base, configuration files, and operating systems.
Knowing the scope of the test beforehand is an excellent way to help the organization plan a penetration testing budget and determine which pen test software should be used.
Account for testing methodologies to be used
Penetration testing can be conducted using different methodologies, such as black box, white box, or gray box testing. Evaluate the software’s capability to support the desired testing methodology. Some tools may specialize in specific types of testing, so be sure to check that the software aligns with your preferred approach. Flexibility in supporting various testing methodologies can be beneficial if you require different approaches for different systems or scenarios.
Think about ease of use and user interface
You should consider the software’s user-friendliness and its user interface’s intuitiveness. Penetration testing involves complex processes, so it’s important to choose a tool that is easy to navigate and understand. A well-designed user interface and clear documentation can significantly enhance your experience with the software and improve productivity. While some of the penetration testing tools I shortlisted offer both GUI and command-line interfaces, some only support the command-line interface. Although both interfaces lead to the same result, advanced users may be more comfortable with the command-line interface than average users.
Consider compatibility and integration options
Assess the compatibility of the software with your existing IT infrastructure. Ensure that the tool can seamlessly integrate with your systems, networks, and applications without causing disruptions. In addition, do take into account other compatibility considerations as it relates to operating systems, databases, and programming languages supported by the software.
Additionally, verify whether the tool can integrate with your current security solutions, such as vulnerability management platforms or security information and event management systems.
SEE: SMB Security Pack (TechRepublic Premium)
Include remote resources in testing
Your organization’s penetration testing plans should include your remote resources and employees. Organizations that support remote roles sometimes provide remote access to valuable resources, which can be an entry point for hackers due to poor security monitoring. Remote resources with limited security monitoring systems should be covered in any penetration tests conducted. Excluding remote employees and resources from your pentests defeat the purpose of analyzing your IT infrastructure’s security posture as a whole.
Methodology
To curate our list of the best penetration testing tools, I researched extensively by extracting information from official websites, product documentation, case studies, and user feedback from reliable third-party review sites. The criteria that informed our choice include the key features and functionalities covered by the pen testing solution, the software’s community, the software’s user base/popularity, ease of use, and the quality of documentation offered. All these factors informed our selection process for this review.
Luis Millares updated this article.
